Research Fields

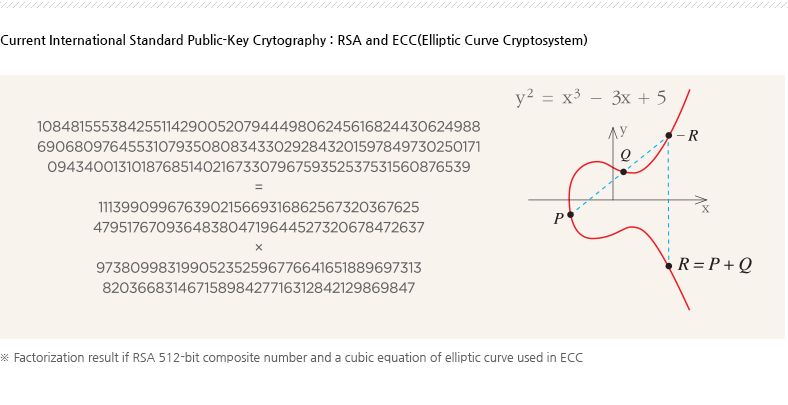
Development of High-Speed Public-Key Cryptographic Algorithms based on Mathematical Hard Problems
Development of High-Speed Public-Key Cryptographic Algorithms based on Mathematical Hard Problems
There have been reported various hacking cases on the Internet of Things(IoT) including smart fridges, automated toilets, self-driving cars and healthcare devices.
Cryptographic algorithms can prevent economic and personal damages caused by these hacking in IoT environments.
There are restrictions on using current international standard public-key cryptographic algorithms for resource constrained IoT devices due to their slow speed and high energy consumption.
The cryptographic technology research team of NIMS is developing next generation public-key cryptographic algorithms suitable for IoT devices and secure against quantum computing attacks.
Key Research Content
- Security analysis of public-key cryptographic algorithms based on various mathematical hard problems
- Design of new cryptographic algorithms, their security analysis against algebraic attacks and optimal implementations on resource-constrained IoT devices
- Security analysis of public-key cryptographic algorithms against side-channel attacks and study on their countermeasures
- Applications of the public-key cryptographic algorithms to device authentication and Blockchain
- Design of privacy-preserving protocols based on the cryptographic algorithms with anonymity, unlinkability and traceability