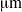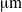Butterfly species identification by branch length similarity entropy
Kang, Seung-Ho; Jeon, Wonju;Lee, Sang-Hee
|
JOURNAL OF ASIA-PACIFIC ENTOMOLOGY
15
(2012)
- 초록
We previously developed a shape recognition methodology that uses “branch length similarity” (BLS) entropy, which is defined as a simple branching network consisting of a single node and branches. The simple network is referred to as a “unit branching network” (UBN). Our approach involves obtaining BLS entropy profiles from UBNs created by joining each pixel in the outline of a shape with every other pixel in the shape's border. The profiles successfully characterize the shapes by comparing their BLS entropy profiles. Presently, we modified this approach to facilitate its application to butterfly species identification by partitioning and weighting the entropy profile. As a test, we identified the butterfly species Colias erate, Parnassius bremeri, Eurema hecabe, Gonepteryx rhamni, and Papilio maackii. Each species group consisted of 10 specimens. We used wing shape to identify a species. We extracted evenly spaced x–y coordinates of boundary pixels for the wing shapes in a counter counterclockwise direction. The number of the pixels was 749. We then sequentially partitioned 749 x–y pairs into 15 groups, calculated entropy profiles for the groups, and weighted the profiles. The profiles were combined in order, resulting in a single weighted BLS entropy profile for a wing's shape. Subsequently, we statistically compared the correlation coefficient among the weighted BLS profiles. Our experimental results showed that this method was statistically successful for butterfly species identification. The advantage of the partitioning and weighting process in shape recognition is also discussed.
- 초록
We previously developed a shape recognition methodology that uses “branch length similarity” (BLS) entropy, which is defined as a simple branching network consisting of a single node and branches. The simple network is referred to as a “unit branching network” (UBN). Our approach involves obtaining BLS entropy profiles from UBNs created by joining each pixel in the outline of a shape with every other pixel in the shape's border. The profiles successfully characterize the shapes by comparing their BLS entropy profiles. Presently, we modified this approach to facilitate its application to butterfly species identification by partitioning and weighting the entropy profile. As a test, we identified the butterfly species Colias erate, Parnassius bremeri, Eurema hecabe, Gonepteryx rhamni, and Papilio maackii. Each species group consisted of 10 specimens. We used wing shape to identify a species. We extracted evenly spaced x–y coordinates of boundary pixels for the wing shapes in a counter counterclockwise direction. The number of the pixels was 749. We then sequentially partitioned 749 x–y pairs into 15 groups, calculated entropy profiles for the groups, and weighted the profiles. The profiles were combined in order, resulting in a single weighted BLS entropy profile for a wing's shape. Subsequently, we statistically compared the correlation coefficient among the weighted BLS profiles. Our experimental results showed that this method was statistically successful for butterfly species identification. The advantage of the partitioning and weighting process in shape recognition is also discussed.
자세히보기